... you are gonna have a bad day.
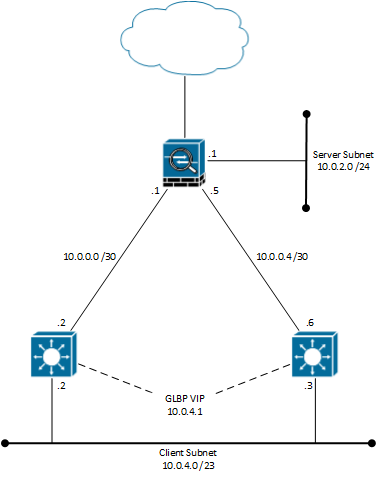
I just had a task, where a network needed to be changed from a layer 2 configuration and into a layer 3 configuration. The network design below is a somewhat simplified replication, that will illustrate the issue with doing dynamic routing on a Cisco ASA firewall.
So, a design using two multi-layer switches configured with GLBP for the client subnet, which are connected to a separate interface of the ASA firewall. OSPF was configured between the ASA and the two MLS routers. The expectation here was that the clients would be load balanced to use each of the MLS routers using GLBP and the MLS routers would then send traffic over their links to the firewall facilitating access from the client network to either the Internet or the server subnet.
However, the mistake I made, when making a up the proof of concept (for the routing part of this setup), was that I replaced the ASA firewall with another router expecting them to handle routing somewhat similarly. When the time came to configure the network I discovered that the ASA did not load balance the trafik over the two links - instead it installed the route to 10.0.4.0 /23 only over one of the two links even though the OSPF database showed that both the MLS routers sent the subnet in their LSAs. The ASA would failover to the other link in case of a link failure, but it only installed the path through one of the two MLS routers into the routing table.
Below is the output of a show route on the ASA (after I borrowed one to lab this up).
ASA# show routeAnd then a show ospf database router command on the same ASA to show the routes from both MLS routers.
<output omitted>
C 10.0.0.0 255.255.255.252 is directly connected, LINK1
C 10.0.0.4 255.255.255.252 is directly connected, LINK2
O 10.0.4.0 255.255.254.0 [110/11] via 10.0.0.2, 1:10:36, LINK1
C 10.0.4.0 255.255.255.0 is directly connected, SERVERS
ASA# show ospf database routerThe route to 10.0.4.0 /23 is received from both the MLS routers, but the route installed in routing table of the ASA is only the one with the next-hop of 10.0.0.2
<output omitted>
LS age: 433
Options: (No TOS-capability, DC)
LS Type: Router Links
Link State ID: 2.2.2.2
Advertising Router: 2.2.2.2
LS Seq Number: 80000008
Checksum: 0x1a7
Length: 60
Number of Links: 3
<output omitted>
Link connected to: a Stub Network
(Link ID) Network/subnet number: 10.0.4.0
(Link Data) Network Mask: 255.255.254.0
Number of TOS metrics: 0
TOS 0 Metrics: 1
LS age: 414
Options: (No TOS-capability, DC)
LS Type: Router Links
Link State ID: 3.3.3.3
Advertising Router: 3.3.3.3
LS Seq Number: 80000007
Checksum: 0xdccc
Length: 60
Number of Links: 3
<output omitted>
Link connected to: a Stub Network
(Link ID) Network/subnet number: 10.0.4.0
(Link Data) Network Mask: 255.255.254.0
Number of TOS metrics: 0
TOS 0 Metrics: 1
I have not found a way to make the ASA behave more like a router in a case like this, but perhaps it was never meant to... The problem here was solved by putting a router in front of the firewall.
I would like to make it clear that I (sadly) do not work much with the Cisco ASA products and this was the first time I actually configured OSPF on an ASA. I made the assumption that it would behave less like a firewall product, when it came to routing, just because it had Cisco stamped on it.
If anyone has any insight to impart regarding dynamic routing configuration on the ASA products please do drop a comment or send me private a message - I would love to have the discussion.